With the support of their sponsor, Ms. Sarah Standard, Cybersecurity/Interoperability Technical Director, Office of the Under Secretary of Defense for Research and Engineering (OUSD(R&E)), SERC researchers are developing test and evaluation processes to improve resilience against cyberattacks. Ms. Standard presented with Dr. Peter Beling of Virginia Tech at the 2022 Annual Research Review.
Ms. Standard provided a definition of resilience as “the ability of a system to provide required capability despite the influence of adversity.” She defined adversity as “the events and conditions that can influence the system’s behavior and outcomes,” and further defined operational resilience as “the ability of systems to resist, absorb, and recover from or adapt to an adverse occurrence during operation that may cause harm, destruction, or loss of ability to perform mission-related functions.” Standard noted a need for more cyberattack resilience testing.
The SERC research applies a systems engineering approach to developing operational resilience. Beling outlined a concept of a FOREST (Framework for Operational Resilience in Engineering and Systems Test) and TREEs (Testable Resilience Efficacy Elements). Each TREE of the FOREST involves a process such as sensing an attack and informing system operators; addressing operator roles and anticipated performances; making resilience decisions; and post-event and lifecycle retesting.
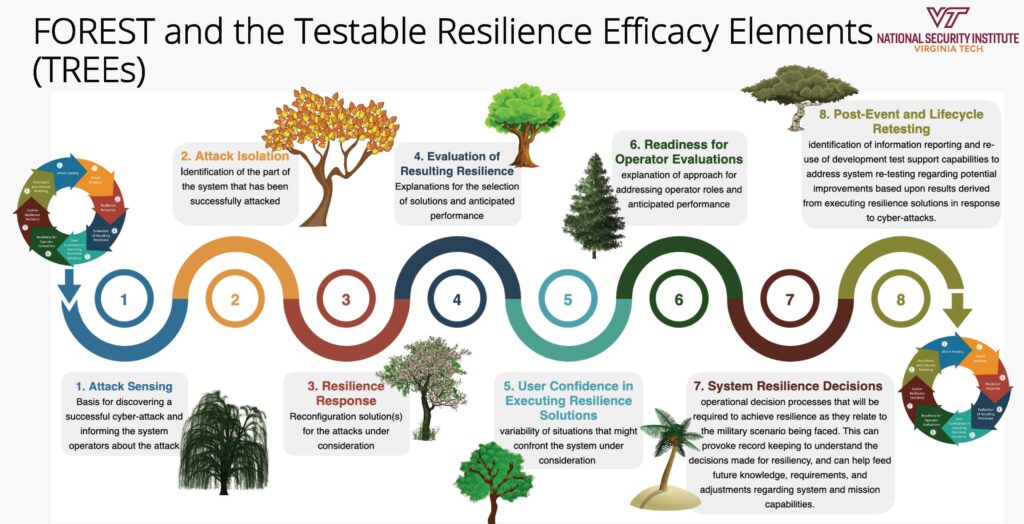
“Every system is going to be different, but we could think about common elements that have to do with operational resilience,” Beling said. “That’s the idea of the FOREST, to provide a way of looking at resilience so you’re writing requirements that are covering some of the ground that has to do with these resilience mechanisms working the way you hope they would in the context of an actual system. That means considering all kinds of strange things you might not have had in mind if you’re just thinking about the engineering aspects. You need to sense an attack, you need to try to isolate it and figure out which subsystems are affected, what is the blast radius of the attack or the extent of the contagion, and what can you trust and what can you not trust.”
Beling discussed the research based on examples of an unmanned aerial vehicle and a fictious land defense system. “The exciting thing about this project is that it’s a pilot on a real weapons system,” he said. “It’s a major program that exists in the digital world. We have a lot to work with in terms of a set of models and a digital framework that the program has been following.”
Watch a recording and download slides of this presentation, and learn more about the next phase of the research. Follow the SERC on LinkedIn for updates on systems engineering research.

